So, we are used to mentioning the risks that exist when browsing unprotected, open fraudulent links that reach us by email, or downloading applications from unsafe sources. Today we are going to mention about USBHarpoon, a different method that uses a simple USB cable to infect the victim.
USBHarpoon – A BadUSB Attack With A Twist
There are many ways in which our devices can be compromised. Many methods by which a cybercriminal can easily infect a computer. So, we are used to mentioning the risks that exist when browsing unprotected, open fraudulent links that reach us by email, or downloading applications from unsafe sources. Today we are going to mention about USBHarpoon, a different method that uses a simple USB cable to infect the victim.
USBHarpoon, the attack that uses a USB charging cable
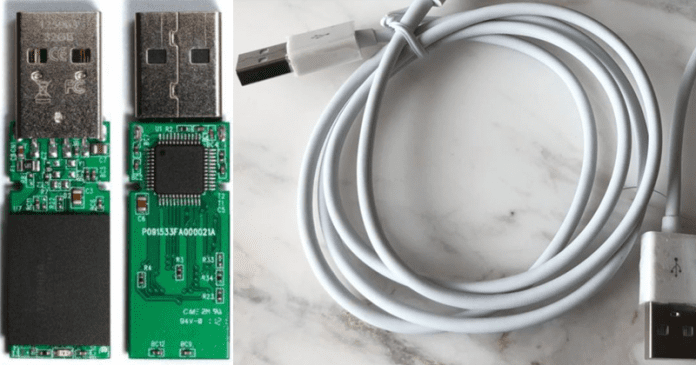
It should be noted that this is only a test that has been carried out by security researchers. It is a malicious version of a USB cable that is reprogrammed with a chip. This causes it to appear on the computer as a human interface device (HID). This type of attack is called BadUSB. It could be anything. For example a simple USB keyboard, a mouse, a memory card etc. After a malicious configuration, they could issue a succession of commands. This group of security researchers used what they have termed as USBHarpoon to replace the USB drive with a charging cable. This is something that users would not be too careful about. We already know that nowadays we can find this type of cable in many airports, train stations, shopping centers, as they are useful to charge our devices in a moment of urgency. It is not something new since previously there have been attempts to create something similar. However, on this occasion, they have achieved it. A simple USB cable, fully functional for use, has been modified in a malicious way to attack the device. This cable would work properly to charge. The user, therefore, at first could not suspect anything and would continue with its normal use. One of the researchers reported that today users may suspect USB devices. For example, a memory or a keyboard, as we have indicated. However they would not suspect, or at least it would be more complicated to notice a normal malicious charging cable. Moreover, security researchers have reported that such attacks would work correctly on a USB Type C.
What about its work on unlocked devices?
This type of attack would be successful on devices that have been unlocked. This would allow downloading commands and run them easily. It would affect different operating systems such as Windows, Linux or Mac. Of course, this whole process is visible on the screen. The attacker, therefore, would have to hide it in some way.
As we have mentioned, this is simply a test that has been carried out by a group of security researchers. However, you could move to real life in this way or similar. That is why we must always be careful when connecting our devices to unknown places. It is tempting to put the mobile phone in a station, for example, when we have little charge, using a cable used by many users. We really do not know what can be behind it. Therefore always use common sense and, if possible, avoid this type of cable that we find in public places. It is better to carry our own charger and find the time to plug it. So, what do you think about this? Simply share all your views and thoughts in the comment section below.
Δ