KillDisk, turned into a fake ransomware It is really a new version of KillDisk malware. Its function is to erase hard drives. However, on this occasion, this variant is passed by a ransomware. This fake ransomware deliberately deletes the hard drive but also includes a ransom note. An attempt to trick the victim into thinking that it is a ransomware and that if they pay, they will retrieve their folders. KillDisk is one of the most lethal types of malware. The erase of hard drives is its function. Something that obviously harms users a lot. It has been used mainly by cyber-espionage groups, such as Telebots. This is the same group that created the Sandworm malware that attacked industrial equipment in the United States. Also, the BlackEnergy malware that was used in attacks against the Ukrainian electricity grid, and the NotPetya ransomware that hit many companies in June 2017. KillDisk was initially developed as a disk-erase malware that was implemented in the later stages of an infection, so attackers could use it to hide their fingerprints by cleaning discs and destroying all forensic evidence. This was the main goal of KillDisk when it was used together with the BlackEnergy malware during the Telebots attacks on the Ukrainian electricity network in December 2015 and December 2016.
Changes
At the end of 2016, KillDisk received a facelift and started posing as ransomware in attacks against Ukrainian banks. A variant of Linux has discovered shortly after, which was used against the same objectives. Now, Trend Micro reports on new KillDisk attacks. The company says it has detected a new version, but the changes are minimal compared to past attacks. The ransom note is still there, as well as the disk erases functions. The only thing that has changed is the objectives, with KillDisk deployed in the networks of financial firms in Latin America, far from the previous objectives of Ukraine where malware was detected in the last three years. At the moment, Trend Micro did not say whether these more recent attacks were carried out by the TeleBots team, or by some imitators who try to trick the researchers and mislead them. But as in previous attacks, the researchers also noticed that KillDisk was not the main malware deployed.
Functioning
According to the researchers, KillDisk, once it enters the computer, loads into memory, deletes the files and changes the name. Then, it will overwrite the first 20 sectors of the Master Boot Record (MBR) of each storage device with 0x00 bytes. After that, it will rewrite the first 2800 bytes of each file with the same 0x00 bytes in each fixed and removable storage unit. The only files that remain intact are the files and folders found in the following directories, all related to operating system operations:-
WINNT Users Windows Program Files Program Files (x86) ProgramData Recovery (case-sensitive check) $ Recycle.Bin System Volume Information old PerfLogs
Later it initiates a timer of 15 minutes and kills the following processes, that are fundamental for the operating system. This causes the computer to restart without the user’s option:-
Client/server run-time subsystem (csrss.exe) Windows Start-Up Application (wininit.exe) Windows Logon Application (winlogon.exe) Local Security Authority Subsystem Service (lsass.exe)
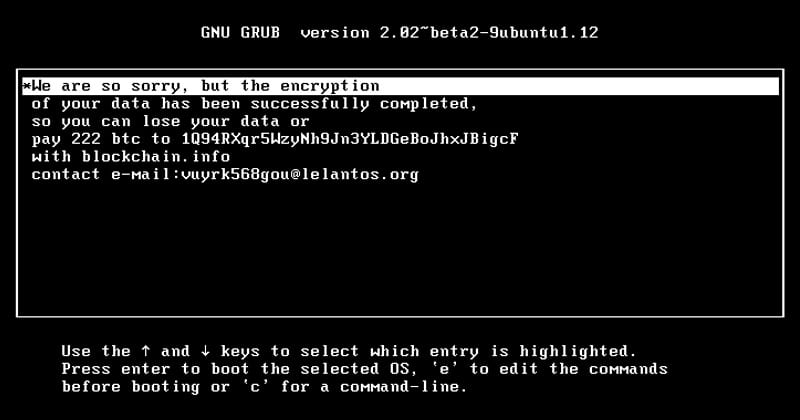
Once the system is rebooted, the user will not be able to use their computer unless they repair the damaged MBR records. When a system administrator investigates, the most common scenarios are that they will find the ransom note and believe that the system was attacked by a ransomware. So, what do you think about this fake ransomware? Simply share all your views and thoughts in the comment section below.
Δ